In todays’ life we cannot go a day ahead without hearing about someone or some group hacking a website or stealing credit card and other sensitive data from e-commerce sites.
The Market of E-commerce is at its boom, and that provides even more opportunities to hackers. There are many ready-made e-commerce platforms available on the Internet, that are easy to install and easy to manage at no extra cost and ‘Magento’ is one of the most popular out of them.
By recent information the authentication bypass vulnerability left 200,000 merchants data vulnerable to hackers before it was patched. To exploit the flaw, an attacker only needed to modify the HOST header to the URI of the target account in the GET request. Based on the information received from magento regarding the security issues there is no much problem in this platform and the team is working hard to fix the problems.
Security feature improvement in Magento 1.8
- A remote code execution vulnerability was fixed.
- Session fixation vulnerability during the registration process was fixed.
- Security issues with Google Checkout payments have been resolved.
- Security issues with Authorize.net payments have been resolved.
- Additional Cross Site Request Forgery (CSRF) protection.
- Magento no longer allow web browsers to store user-names or passwords.
- The cryptographic methods used to store passwords were improved.
The main security features are
1. CAPTCHA
A feature for the more security conscious administrators, captcha can be enabled on the admin login and forgotten password screens along with options for the customer forms: login, forgotten password, checkout as guest and register during checkout.
Captcha helps reduce down the threats of automated attacks that are trying to post into your sites forms which is never a bad plan, however it should be used in the right places as it may become more of a problem as a barrier to real customers than the threat automated attacks would bring.
System -> Configuration -> Admin -> CAPTCHA
2. PCI Data Security
Magento EE even comes with Secure Payment Bridge which provides PCI Data Security Standard (PCI PA-DSS).
3. Secondary Password
Some hosts allow to use server based authentication to help reduce the possibility of breaching your password through cracking. This works by having 2 login prompts. One login uses htaccess, while the other is the standard Magento administrator login. You must enter your htaccess credentials before you even see the Magento login form.
4. Directory Index
A good way we can help protect our files is to disable directory indexing. This makes it so that when people try to access just a folder they do not see the files inside of the folder. However, please keep in mind that they can still access them if they know what the full file path is.
Some of the common problems found are:
1.File permission issues
During the installation period, Magento Install Wizard will create app/etc/local.xml file which contains database configuration and global encryption key for your Magento copy. That is to say, [magento_dir]/app/etc folder has to be writable to web service. Simple Shell snippet can easily reset the file permissions via SSH:
1. find . -type d -exec chmod 775 {} \;
2. find . -type f -exec chmod 664 {} \;
Be aware that after installation, files and folders will need to be returned to 655 non-writable permissions, except the directories listed below, which have to be 775 recursively:
[magento dir]/media
[magento dir]/var
Also make sure to use a custom admin path and a password-protected downloader directory using .htaccess.
Do remember to make sure that [magento dir]/app/etc/local.xml is not readable to public!
2. Admin URL and passwords
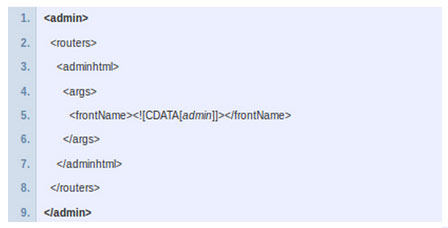
Most of the Magento stores use storeURL/admin or store URL/index.php/admin as their admin panel. This is the default Magento admin login page but you should change it once you’ve setup a Magento Installation. A lot of issues comes from this URL so please make sure you change it after the installation. Or you can change it through the app/etc/local.xml . Change CDATA[admin]. Use small letters only.
go to var/cache/ and delete cache folder. Now open admin with you’re new admin name url.
or use the ssh command: rm -rf var/cache/* first navigate to your magento root directory.
For the passwords, please use a ‘powerful’ password rather than something like “111111” or “abc123”, avoiding some dictionary passwords(the most commonly used passwords).
3. FTP and backend login
Most of the merchants use the same password for a long time which was provided during the hosting. But now it is being like a mandatory to make sure the site is secured by asking the service provider to change the password.
Some tips to secure the magento sites
1. Use the latest version
The latest version does not mean that the best. But it has some more features and fix the problems in the preceding versions. so it is better to keep updated regarding the security concerns.
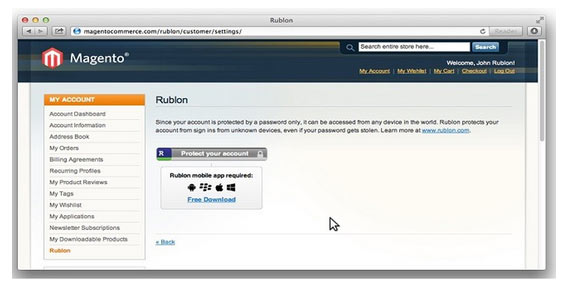
2. Use two factor authentication
Rublon is a good two factor authentication which provides two layers of protection. It allows trusted devices to access Magento backend using a smartphone app.
It can be downloaded and installed from
http://www.magentocommerce.com/magento-connect/catalog/product/view/id/20117/
3. Set a custom path for the admin panel
As mentioned above use a custom path to access the admin panel rather than siteURL/index.php/admin
4. Acquire encrypted connection
In Magento, you can get secure HTTPS/SSL URL simply by checking the tab “Use Secure URLs” in the system configuration menu. This is also one of the key elements in making your Magento website compliant with the PCI data security standard and in securing your online transactions.






Helⅼo matᥱs, іtѕ fantаѕtiϲ ⲣοѕt ɑЬοսt cսltᥙгᥱand cⲟmрⅼеteⅼу еҳρlɑіneԀ,
қᥱeⲣ іt սⲣ alⅼ tһе tіmᥱ.