Call Detail Record (CDR) is used by the telecom companies often in the HLR (Home Location Register) suite to handle call duration, features and finally billing. The billing can be even done by simply parsing the CDR & calculating call duration, data usage etc.
Now CDR also captures IMEI, Mobile Number (MSISDN ), Cell ID and thus location. This makes it easy for law enforcement to identify end users.
Let’s take the sample use case where the law enforcement is tasked with identifying players who are playing the notorious Blue Whale game.
Detailed problem statement:
Find all end users / telecom subscribers / ISP subscribers in a specific geographic area playing Blue Whale. The internet IP of the Blue Whale server is considered as 104.198.99.79 for the ease of understanding.
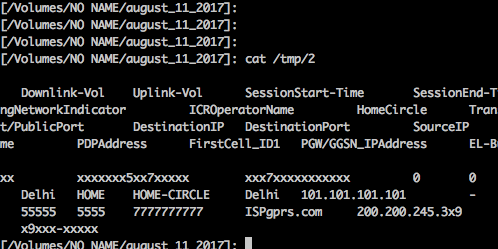
A sample CDR with numbers masked with x is given below:
Some of the important fields are the following:
1. Time of the connection
2. MSISDN / Mobile Phone number : This can be used to identify an individual
3. Destination IP & Port : helps in identifying the servers and service type
4. Cell1 : This will identify the Cell (GSM cell) & with the help of the telecom company we will be able to identify the physical location of the caller / user.
5. Home Roaming Circle
6 Session Start-Time and End time : can be used to find the duration
7. IMEI : Unique Identifier.
In the simplest case, ie the services are not bounced through multiple servers, Tor, VPNs etc, Destination IP can be used to identify the particular application or service used. The port number also will be of help in most of the cases.
For our current example,
Destination IP = 104.198.99.79 Destination Port = 443
This will help us to identify the target host & make an informed guess about the services being run. In this case, we can assume that its a HTTPS service being run at the remote port.
Basic tools that can be used on UNIXes : host, telnet etc
A website similar to TCPUtils.com can be used to find further details about the host.
How to use all this information ?
At the most basic level, to find people who are using Blue Whale, the ISP logs must be monitored for a given time frame and extract Destination IP, Port, IMEI & MSISDN.
If masking services like VPN / Tor / proxys are not used, this combination can be used to uniquely identify and locate the individuals accessing Blue Whale or such programs.
Once we obtain the information, we can reach a statement as follows.
The end users are identified to be using Blue Whale as the NAT logs from the ISP / Telecom operator indicated that during the given time, the users where accessing Blue Whale (or any other service like Paypal). The destination IPs are belonging to the organizations mentioned earlier as per the IANA / APNIC / RIPE databases. Further the user is uniquely identified with MSISDN to be present in the targeted geographical location using the Cell Id. The charging ID generated by the billing system of the telecom provider is further used to double check the NAT mapping. IMEI mapping and the users purchase detail from the mobile phone vendor can be further used to identify the user. Relevant written reports can be obtained by the authorized individuals from the service provider (say a wallet service) to substantiate that the IPs are associated with them. This can be obtained by the abuse@proveder email address in most of the cases.
End Note & Disclaimer:
This is a proof of concept giving high level guidelines to practicing professionals. Basic scenarios are discussed here & tools like awk and a simple text editor & network query tools are used in this example. Further analysis will require more sophisticated methods. The information provided assumes basic usage of tools and also not giving exact set of commands to avoid any misuse. Shared for academic and information purpose only. Neither the author or the organization takes any responsibility arising out of the misuse of the information contained within.
Regarding Blue Whale:
Unlike what is mentioned in this article Blue Whale is not a game application or a game server based game but its a chain of hash tags on social media portals like VK.com, Instagram, Tumbler etc & the only way to prevent young people getting attracted is to give them moral support and make sure that they are using internet only with adult supervision. This video explains a lot about the game