Using HTTP/2 and strict transport security is no more a recommended scenario but a mandatory requirement now. HSTS aka HTTP Strict Transport Security, SNI and higher bit length for key exchange security is supported by all modern browsers, say 4096 – bit Diffie–Hellman–Merkle algorithm. ie to establish secure connection between the web clients and the servers, the keys should be exchanged avoiding MITM (man in the middle attacks). Using better key exchange mechanisms is a way to start.
Here is an example of a reasonably secure NGINX configuration to achieve the same. NGINX is used as it can be used for REST APIs, web services, as well as a reverse proxy capable of terminating SSL connections.
NGINX supports SPDY for a while and from 2015 its supporting HTTP/2 as well.
The configuration file has all the necessary commands listed. Note that apart from the domain name, no IPs are used. Just replace the domain name with any domain and it will work fine for any domain. Also this will work on most of the shared hosting scenarios.
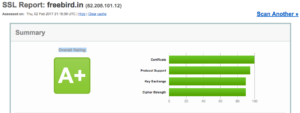
This configuration can give A+ on SSL labs 🙂